iOS Privacy Evolution|Apple's Principles and Feature Enhancements
Explore how iOS has advanced privacy protections while maintaining user convenience, detailing Apple's core privacy principles and key feature updates that safeguard your data effectively.
点击这里查看本文章简体中文版本。
點擊這裡查看本文章正體中文版本。
This post was translated with AI assistance — let me know if anything sounds off!
Table of Contents
The Past and Present of iOS Privacy and Convenience
Apple Privacy Principles and iOS Privacy Protection Features Over the Years
Theme by slidego
[2023–08–01] iOS 17 Update
Additional notes on the latest iOS 17 privacy updates from the previous presentation.
Link Tracking Protection
Safari automatically removes tracking parameters from URLs (e.g., fbclid, gclid, etc.)
Example:
https://zhgchg.li/post/1?gclid=124will becomehttps://zhgchg.li/post/1after clicking.Currently testing iOS 17 Developer Beta 4,
fbxxx,gcxxx, etc. are removed, whileutm_parameters remain; it is unclear if the official iOS 17 or future iOS 18 will improve this further.To see the effect under the strictest conditions, you can install the iOS DuckDuckGo browser for testing.
For detailed test information, please refer to the excellent article “iOS17 Safari’s new feature removes fbclid and gclid from URLs.”
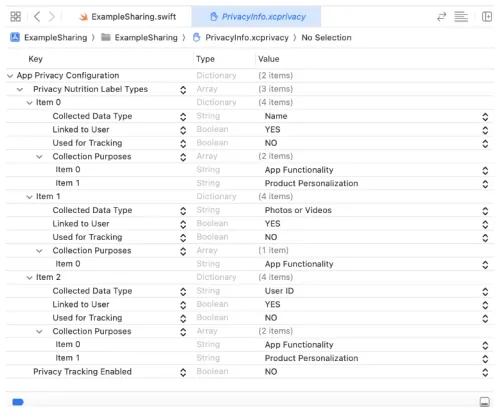
Privacy Manifest .xprivacy & Report
Developers must declare the User Privacy used, and also require the SDKs used to provide their Privacy Manifest.
Also added third-party SDK Signature
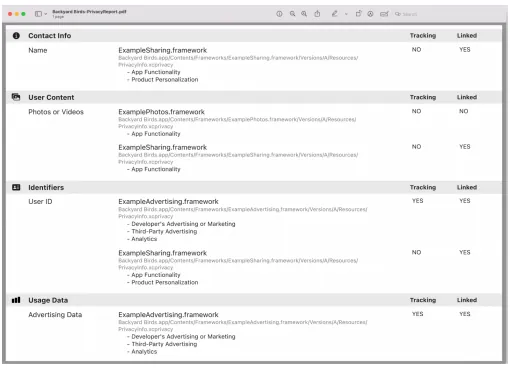
XCode 15 can generate a Privacy Report through the Manifest for developers to set app privacy on the App Store.
Required reason API
To prevent potential misuse of Foundation APIs that could lead to fingerprinting, Apple has started to regulate certain Foundation APIs; you need to declare the purpose of use in the Manifest.
Currently, the more impactful one is UserDefault, which is an API that requires declaration.
1
2
3
Starting from Fall 2023, if your new app or app update uploaded to App Store Connect uses APIs that require a declared purpose (including those from third-party SDKs), and you have not provided an approved purpose in the app's privacy manifest, you will receive a notification. From Spring 2024, to upload a new app or app update to App Store Connect, you must specify the approved purpose in the app's privacy manifest to accurately reflect how your app uses the relevant APIs.
If the current approved purposes do not cover a use case for an API that requires a declared purpose, and you believe this use case directly benefits your app users, please let us know.
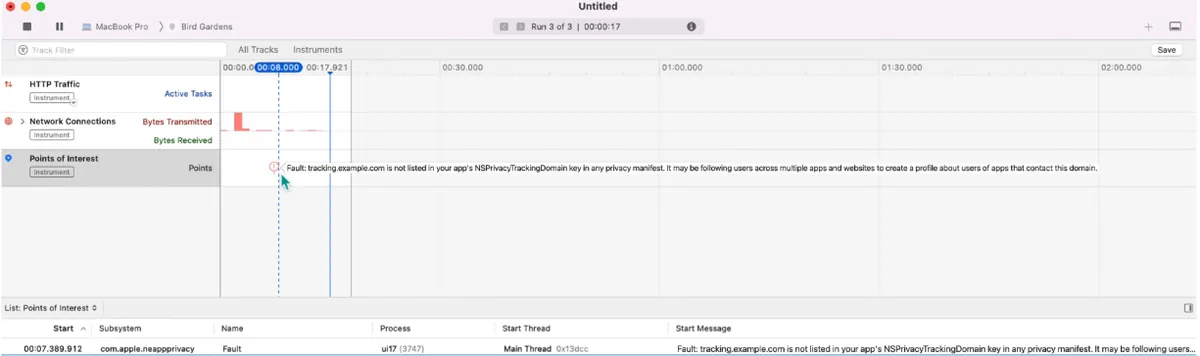
Tracking Domain
The API domain for sending tracking information must be declared in the privacy manifest .xprivacy and network requests can only be initiated after the user consents to tracking. Otherwise, all network requests to this domain will be blocked by the system.
You can check if the Tracking Domain is blocked using the XCode Network tool:
Currently, Facebook and Google’s tracking domains are detected and must be listed as tracking domains according to regulations and permissions must be requested.
graph.facebook.com : Facebook-related data statistics
app-measurement.com : Google-related data statistics: GA/Firebase….
Please note that FB/Google data statistics may significantly decline after iOS 17 because without permission requests and tracking consent, no data will be collected; based on past implementations of tracking permission requests, about 70% of users choose not to allow tracking.
Developers’ own API calls for sending tracking also need to comply with the tracking domain regulations mentioned above by Apple.
If the Tracking Domain and API Domain are the same, a separate Tracking Domain must be created (e.g. api.zhgchg.li -> tracking.zhgchg.li)
Currently, it is unclear how Apple manages developers’ own tracking. Testing our own with XCode 15 has not been detected.
It is unclear whether the officials will use tools to detect behavior or rely on manual review by staff.
fingerprinting is still prohibited.
Introduction
I am honored to participate in the MOPCON Talk, but due to the pandemic, it was held online, which is unfortunate as I couldn’t meet more new friends. The topic of this talk is “The Past and Present of iOS Privacy and Convenience,” where I mainly want to share Apple’s privacy principles and the adjustments in iOS features over the years based on these privacy principles.
iOS Privacy and Convenience: Past and Present | Pinkoi, We Are Hiring!
I believe developers and iPhone users have become quite familiar with the following feature adjustments over the past few years:
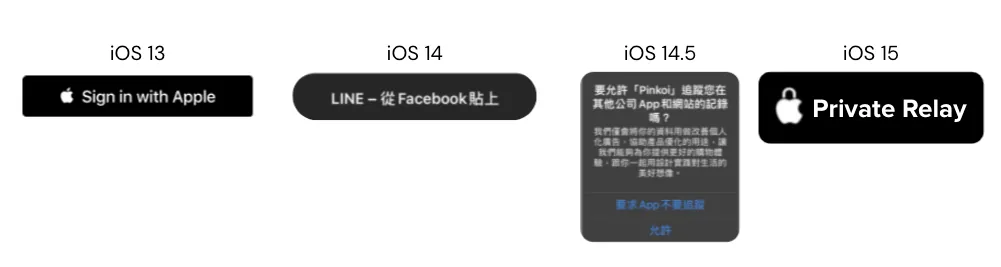
iOS ≥ 13: All apps supporting third-party login must implement Sign in with Apple, or they cannot be successfully published on the App Store.
iOS ≥ 14: Clipboard Access Alert
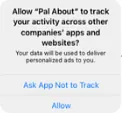
iOS ≥ 14.5: IDFA must be allowed before access, effectively blocking IDFA.
iOS ≥ 15: Private Relay uses a proxy to hide the user’s original IP address
iOS ≥ 16: Clipboard access requires user permission
….and many more, which I will share with everyone at the end of the article
Why?
If you don’t understand Apple’s privacy principles, you might wonder why Apple has been constantly clashing with developers and advertisers in recent years. Many features that users are accustomed to have been blocked.
After watching “WWDC 2021 — Apple’s privacy pillars in focus” and reading “Apple privacy white paper — A Day in the Life of Your Data,” I was awakened to the fact that we have unknowingly leaked a lot of personal privacy. Advertisers and social media platforms have profited greatly, reaching an all-pervasive level in our daily lives.
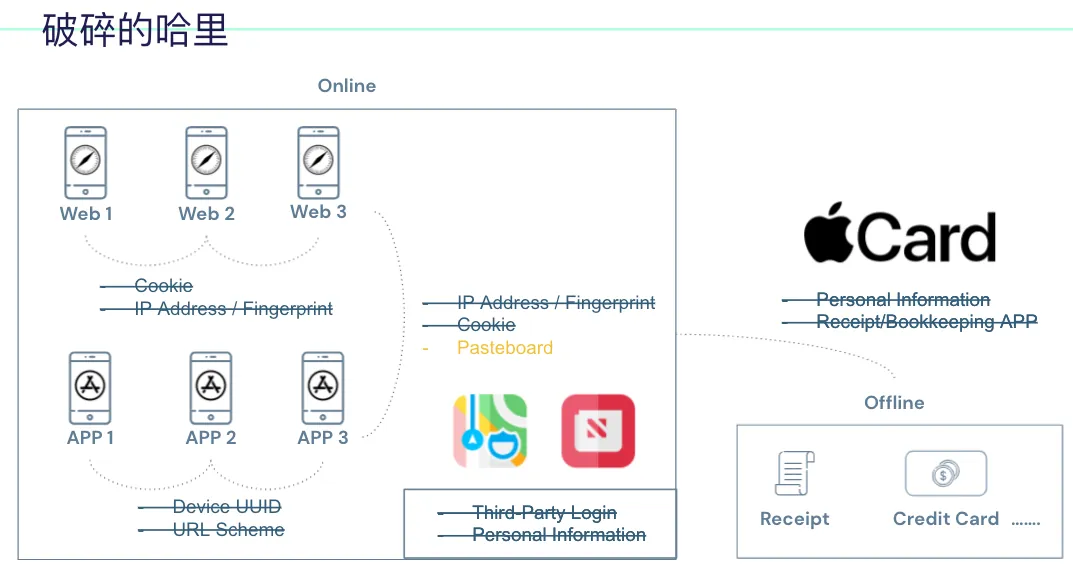
Referencing Apple privacy white paper, the following example uses a fictional character, Harry, to explain how privacy can be leaked and the potential harms it may cause.
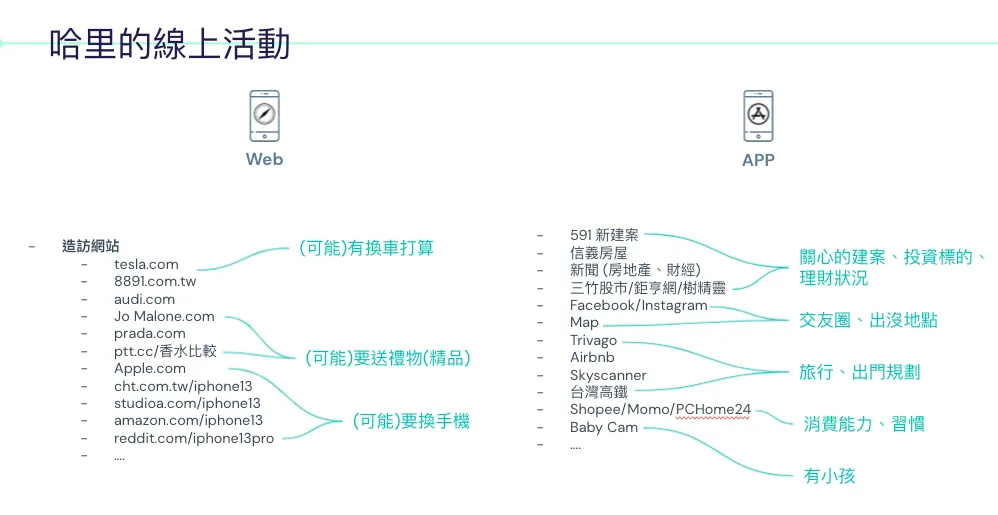
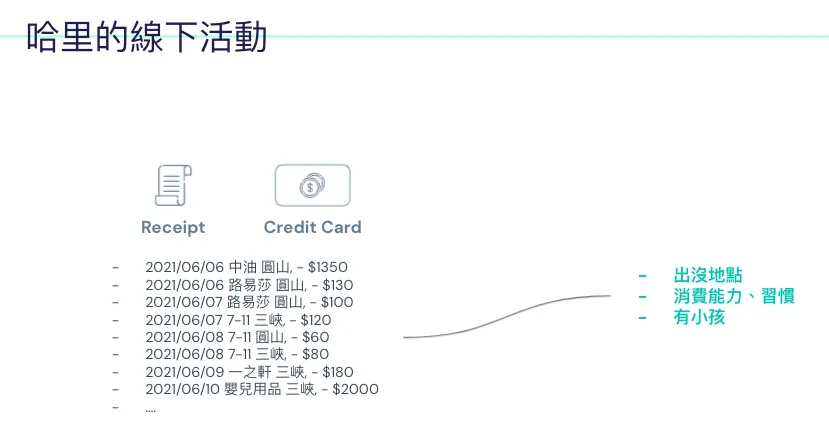
First is Harry’s usage record on the iPhone.
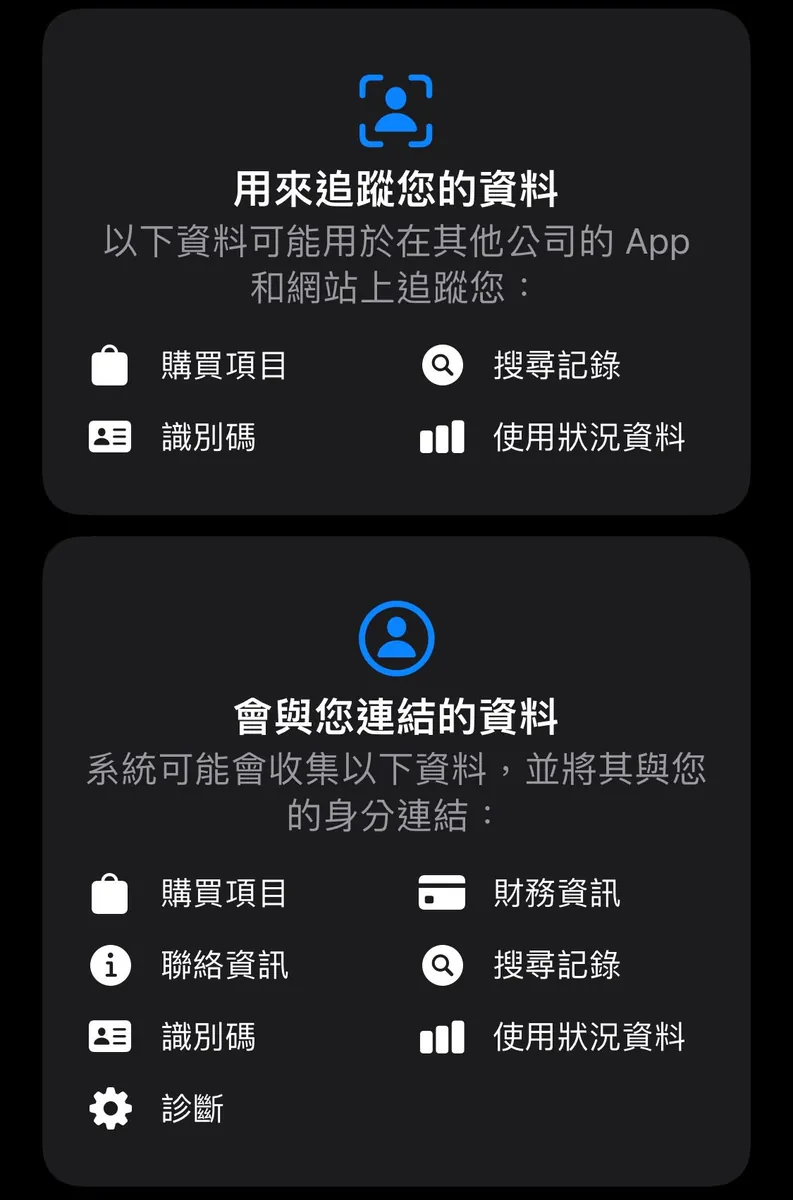
On the left is the web browsing history: You can see visits to websites related to cars, iPhone 13, and luxury goods.
On the right are the installed apps: Investment, travel, social, shopping, and even a baby monitor… these apps
Harry’s Offline Life
Places where offline activities leave records, such as: receipts, credit card transaction records, dashcam footage, etc.
Combination
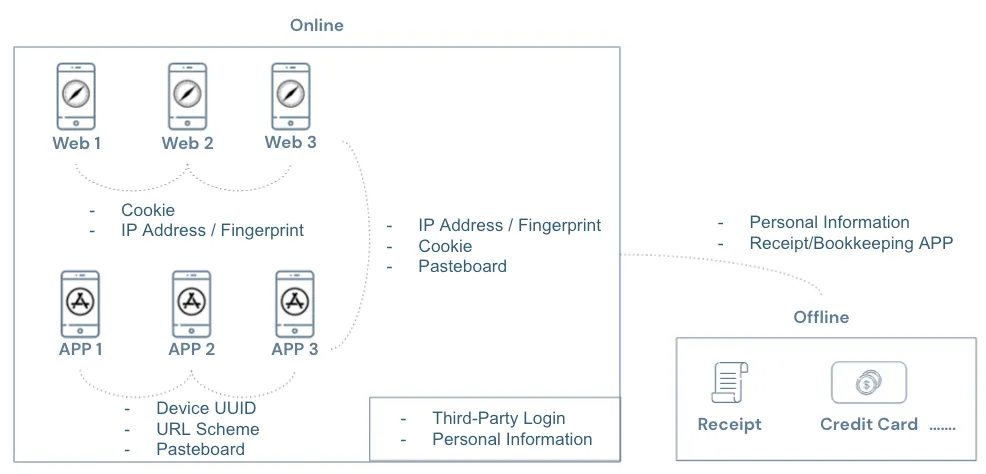
You might wonder how browsing different websites, using various apps (even without logging in), and attending offline events could possibly allow a service to connect all the data together.
The answer is: There are technical means, and it is “possible” or has “already” occurred partially.
As shown in the above image:
When not logged in, websites can identify the same visitor across different sites using Third-Party Cookies or fingerprints calculated from IP address + device information.
When logging in, websites can link your data across sites using registration details such as name, birthday, phone number, email, and ID number.
Apps can identify the same user across different apps by obtaining the device UUID, detecting other installed apps on the phone via URL Scheme, and transferring data between apps through the Pasteboard. Additionally, user registration data can link information after login.
Data can also be transferred between apps and websites using Third-Party Cookies, fingerprinting, and Pasteboard.
The connection between online and offline activities may occur when banks collect credit card transaction records, expense tracking apps, receipt collection apps, dashcam apps, and more. These can link offline activities with online data.
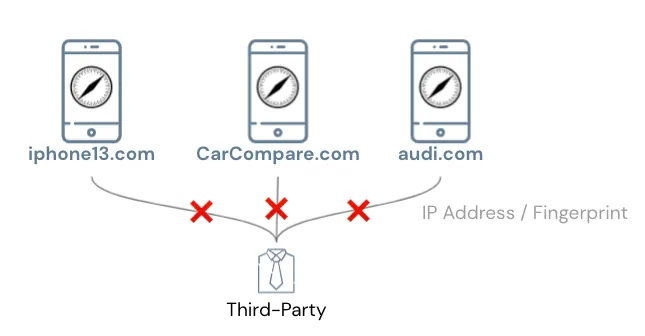
It has been proven technically feasible; so who exactly are the third parties behind all websites and apps?
Large companies like Facebook and Google earn significant revenue from personal advertising; many websites and apps also integrate Facebook and Google SDKs… so it’s hard to say for sure. While some are visible, more often we don’t know which third-party advertising or data collection services websites and apps use, secretly tracking our every move behind the scenes.
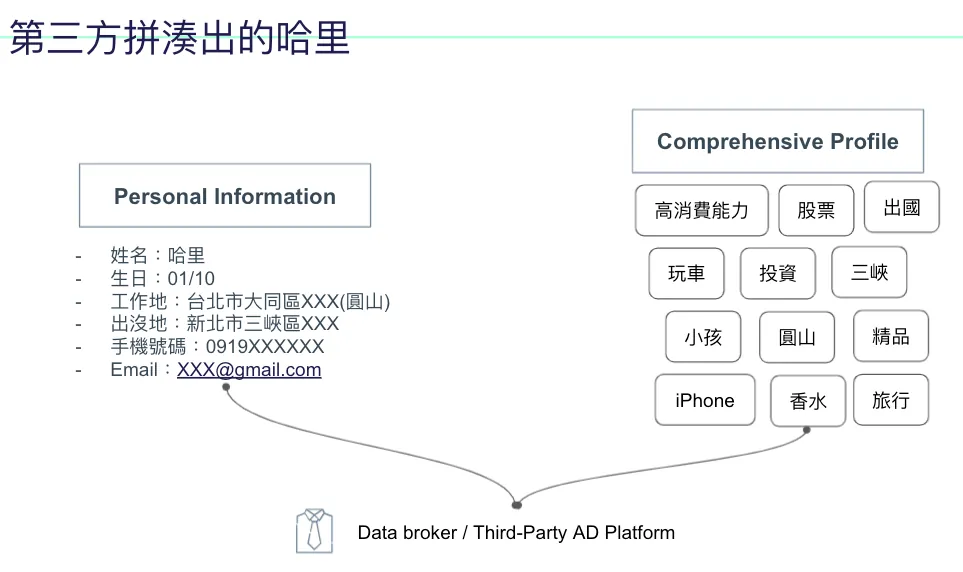
Assuming all of Harry’s activities are secretly tracked by the same third party collecting his data, Harry’s possible profile might look like this:
The left side shows personal information, possibly from website registration or delivery data; the right side displays behavior and interest tags based on Harry’s activity records.
In its eyes, Harry might understand himself even better than Harry does; this data, when used on social media, can make users more addicted; when used in advertising, it can trigger Harry’s overspending or create a cage effect (e.g., recommending you buy new pants, then you buy shoes to match the pants, then socks to go with the shoes… endlessly).
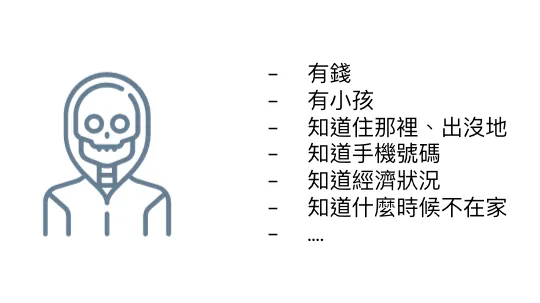
If you think the above is scary enough, there is something even scarier:
Having your personal information and knowing your financial status… if used for malicious purposes, it’s unimaginable, such as kidnapping or theft…
Current Privacy Protection Methods
Legal Regulations (EX: SGS-BS10012 Personal Data Verification, CCPA, GDPR…)
Privacy Policy and De-identification
The main approach is still through regulatory constraints; it’s hard to ensure services 100% always comply, and with many malicious programs online, it’s also difficult to guarantee services won’t be hacked causing data leaks. In short, “if someone wants to do something bad, it’s technically feasible; relying solely on regulations and corporate conscience is not enough.”
Besides, most of the time, we are “forced” to accept privacy policies. We cannot authorize privacy settings individually; either we don’t use the entire service or we use it but must accept all privacy terms. Privacy policies are often opaque, leaving us unaware of how data is collected and used, and whether a third party is secretly gathering our information without our knowledge.
Apple also mentioned that minors’ personal privacy is often collected by services without the consent of their guardians.
Apple’s privacy principles
After understanding the dangers of personal privacy leaks, let’s take a look at Apple’s privacy principles.
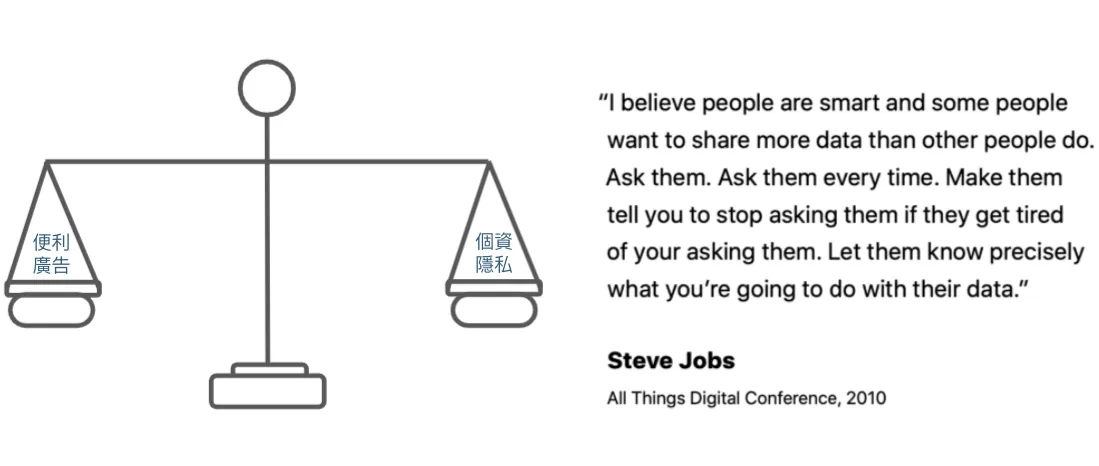
Excerpt from Apple Privacy White Paper: Apple’s ideal is not to completely block but to balance. For example, many people have installed AD Blockers in recent years to fully block ads, which is not what Apple wants; because if connections are completely cut off, it becomes difficult to provide better services.
Jobs said at the 2010 All Things Digital Conference:
I believe people are smart; some are more willing to share data than others. Keep asking them until they get annoyed and tell you to stop. This way, they clearly understand how you intend to use their data. — translate by Chun-Hsiu Liu
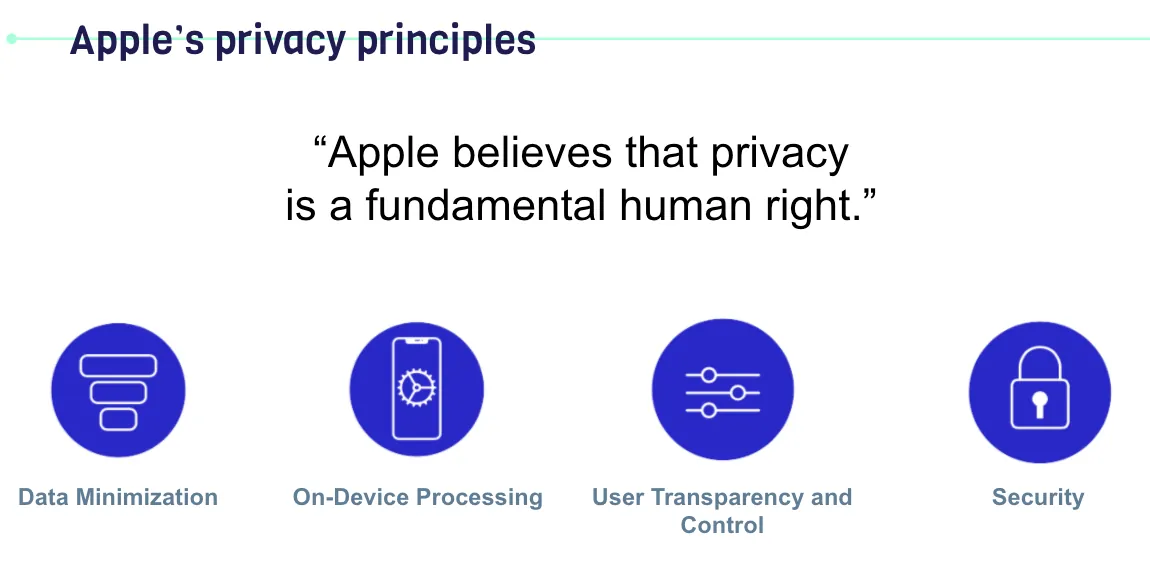
Apple believes privacy is a fundamental human right
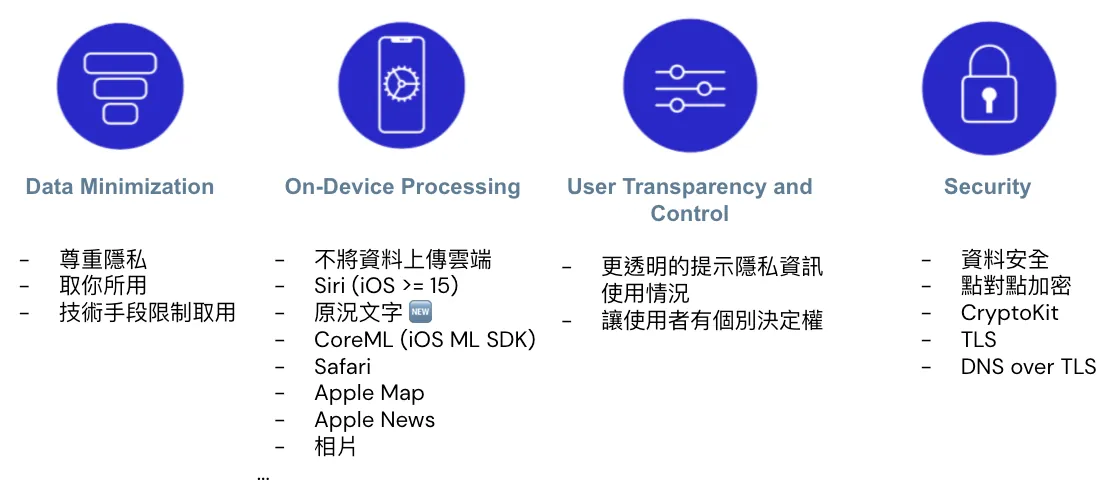
Apple’s Four Privacy Principles:
Data Minimization: Only collect the data you need
On-Device Processing: Apple uses powerful processor chips, and privacy-related data should be processed locally whenever possible.
User Transparency and Control: Inform users about what privacy information is collected and how it is used. Also, allow users to control sharing settings for individual privacy data.
Security: Ensure the safety of data storage and transmission
iOS Privacy-Focused Feature Adjustments Over the Years
After understanding the risks of personal privacy leaks and Apple’s privacy principles, let’s return to the technical side; we can look at the changes iOS has made over the years to protect personal privacy.
Between Websites
Mentioned earlier
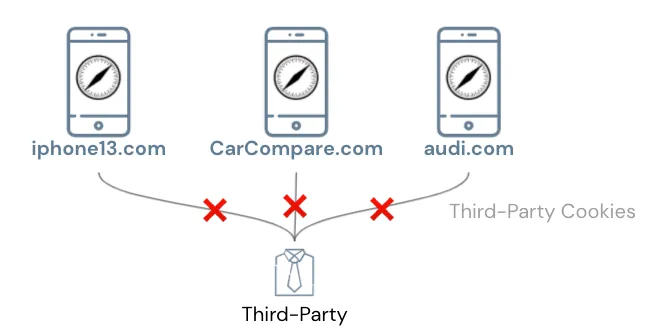
The first method uses Third-Party Cookies to link visitor data across websites:
🈲, Safari on iOS >= 11 has implemented Intelligent Tracking Prevention ( WebKit )
Enabled by default, the browser actively identifies and blocks third-party cookies used for tracking and advertising; each year, the iOS version continuously improves the detection system to prevent misses.
The method of tracking users across websites via Third-Party Cookies is basically no longer feasible on Safari.
The second method is to use the Fingerprint calculated from the IP Address + device information to identify the same browser across different websites:
🈲, iOS >= 15 Private Relay
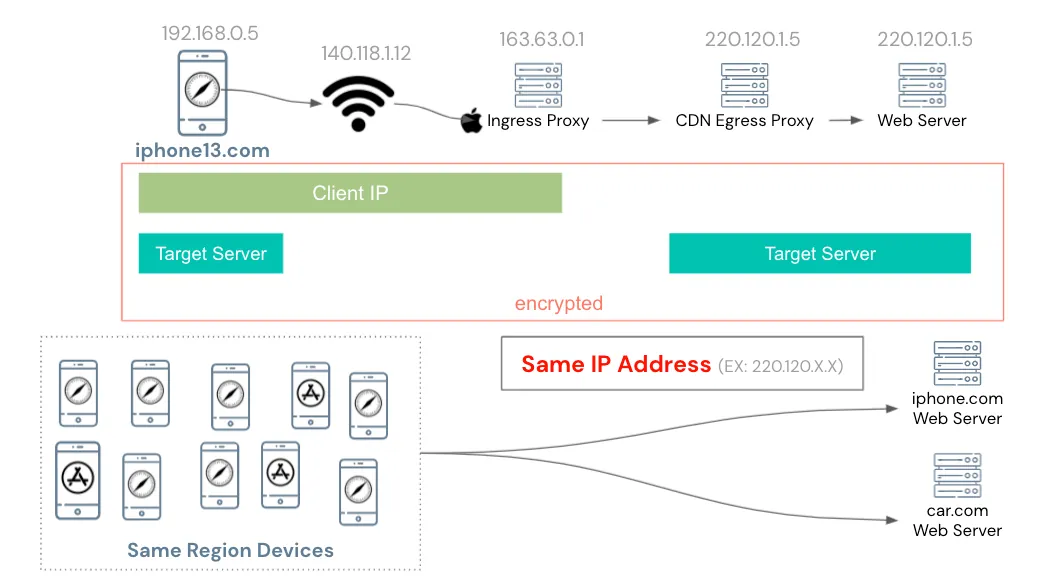
Especially after Third-Party Cookies were banned, more services have adopted this method. Apple is aware of this… Fortunately, in iOS 15, even IP information is obfuscated!
The Private Relay service first sends the user’s original request randomly to Apple’s Ingress Proxy, then Apple randomly assigns it to a partner CDN’s Egress Proxy, which finally requests the target website.
The entire process is encrypted and can only be decrypted by your iPhone’s chip. Only you know both the IP and the target website of the request. Apple’s Ingress Proxy only knows your IP, the CDN’s Egress Proxy only knows Apple’s Ingress Proxy IP and the target website, and the website only knows the CDN’s Egress Proxy IP.
From an application perspective, all devices in the same region use the same shared CDN Egress Proxy IP to request the target website; therefore, the website can no longer use the IP as fingerprint information.
For technical details, refer to “WWDC 2021 — Get ready for iCloud Private Relay”.
Additional Private Relay:
Apple/CDN providers do not have complete logs for tracing:
I investigated how Apple prevents misuse for malicious purposes but found no clear answer; it might be similar to how Apple refuses to unlock criminals’ iPhones for the FBI. Privacy is a fundamental human right for everyone.Enabled by default, no special connection needed
No impact on speed or performance
IP will be guaranteed within the same country and time zone (users can choose a general city), but specific IPs cannot be assigned.
Only effective for partial traffic
iCloud+ users: All traffic on Safari + Insecure HTTP Requests within apps
Regular users: Only effective against third-party tracking tools installed on websites in SafariThe official CDN Egress IP List is provided for website developers to identify (do not mistakenly block Egress IPs, as it may cause widespread issues)
Network administrators can ban DNS to disable Private Relay for all users
iPhone Can Disable Private Relay for Specific Network Connections
Disabling Private Relay When Connecting to VPN/Using Proxy
Currently still in Beta version (2021/10/24). After activation, some services may be inaccessible (China region, Chinese version of TikTok) or services may frequently log out.
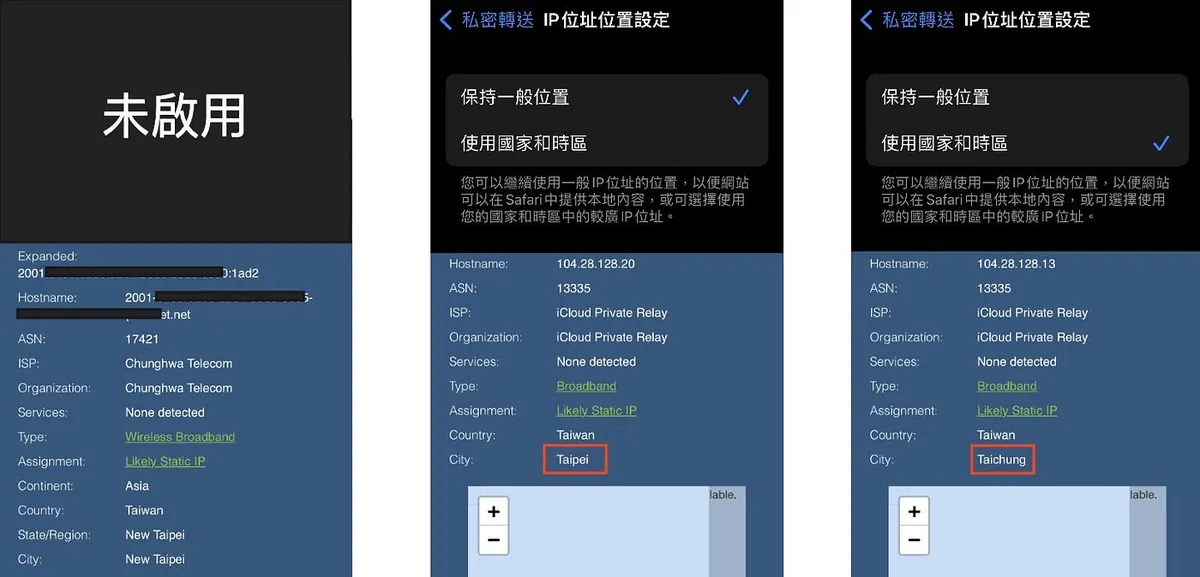
Private Relay Test Images
Figure 1 Disabled: Original IP Address
Figure 2 Enable Private Relay — Keep general location: IP becomes CDN IP but still in Taipei
Figure 3 Enabling Private Relay — Country and Time Zone (Expanded Obfuscation): IP changes to CDN IP & location shifts to Taichung, but the time zone and country remain the same
The app can use URLSessionTaskMetrics to analyze connection records of Private Relay.
Going off-topic, therefore the method of using IP addresses to obtain fingerprints for user identification can no longer be used.
Between Apps
The first method was early access to the Device UUID:
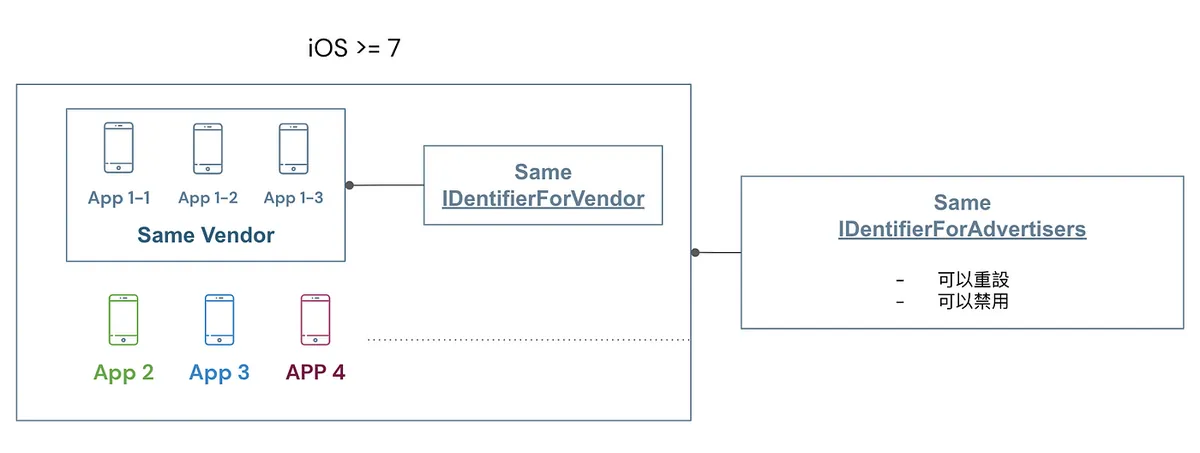
🈲,iOS >= 7 prohibits access to Device UUID,
Using IDentifierForAdvertisers/IDentifierForVendor Instead
IDFV: All apps under the same developer account can access the same UUID; using KeyChain together is also the current method to identify user UUIDs.
IDFA: Different developers and apps can obtain the same UUID, but users can reset or disable the IDFA.
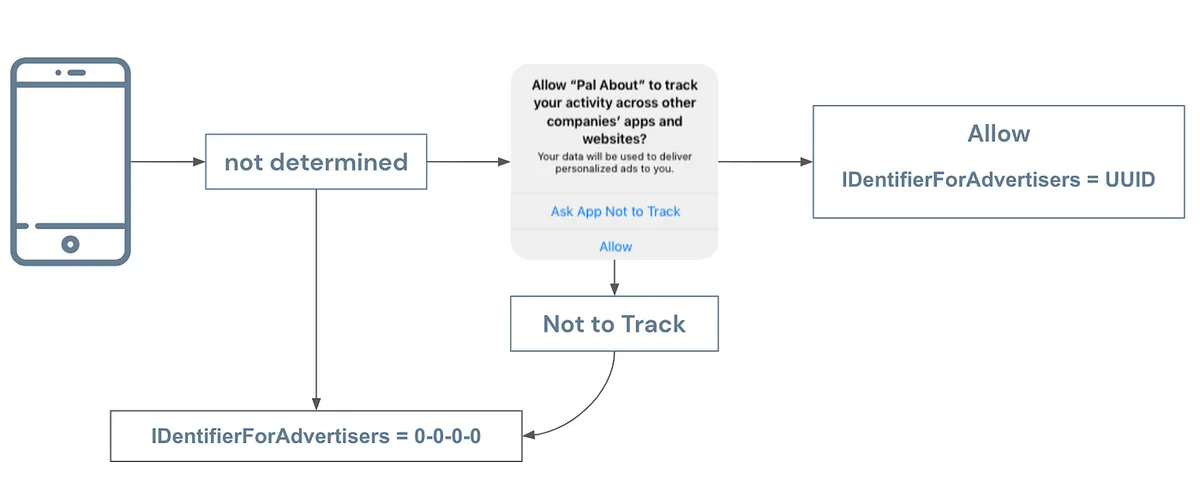
🈲, iOS >= 14.5 IDentifierForAdvertisers requires user consent before use
After iOS 14.5, Apple strengthened restrictions on accessing IDFA. Apps must ask users for permission to track before obtaining the IDFA UUID; if not asked or not allowed, the value cannot be retrieved.
Market research companies’ preliminary data show that about 70% of users (some recent data say 90%) do not allow tracking or access to IDFA, which is why people say IDFA is dead!
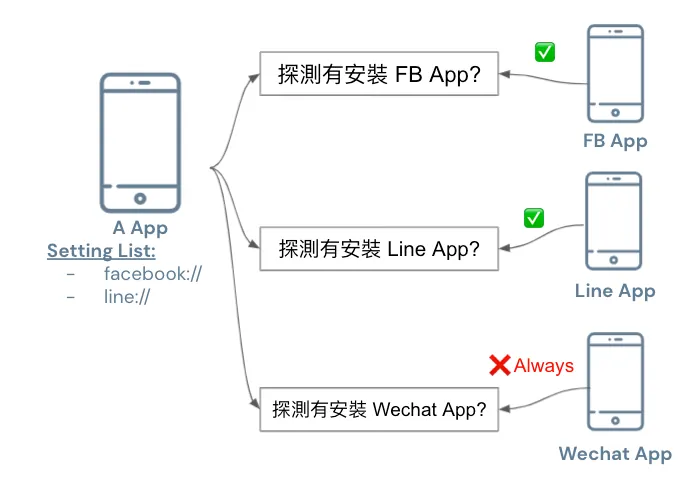
The second method for inter-app communication is URL Scheme:
iOS apps can use canOpenURL to check if a specific app is installed on the user’s device.
🈲, iOS >= 9 requires in-app settings before use; cannot be detected arbitrarily.
iOS ≥ 15 new limitation: you can set up to 50 schemes for other apps only.
Apps linked on or after iOS 15 are limited to a maximum of 50 entries in the LSApplicationQueriesSchemes key.
Between Websites and Apps
As mentioned above
The first method also connects via Cookie:
In early iOS, Safari cookies and App WebView cookies could be shared, allowing data to be linked between websites and apps.
You can secretly insert a 1-pixel WebView component in the background of the app screen to quietly retrieve Safari cookies for use.
🈲,iOS >= 11 Prohibits Cookie Sharing Between Safari and App WebView
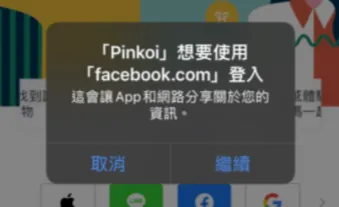
If you need to access Safari cookies (e.g., use website cookies for login), you can use the SFSafariViewController component; however, this component forces a prompt window and cannot be customized, ensuring users are not unknowingly having their cookies stolen.
The second method is to identify the same visitor across different websites using the Fingerprint calculated from the IP Address + device information on the same website:
As mentioned before, iOS ≥ 15 is obfuscated by Private Relay.
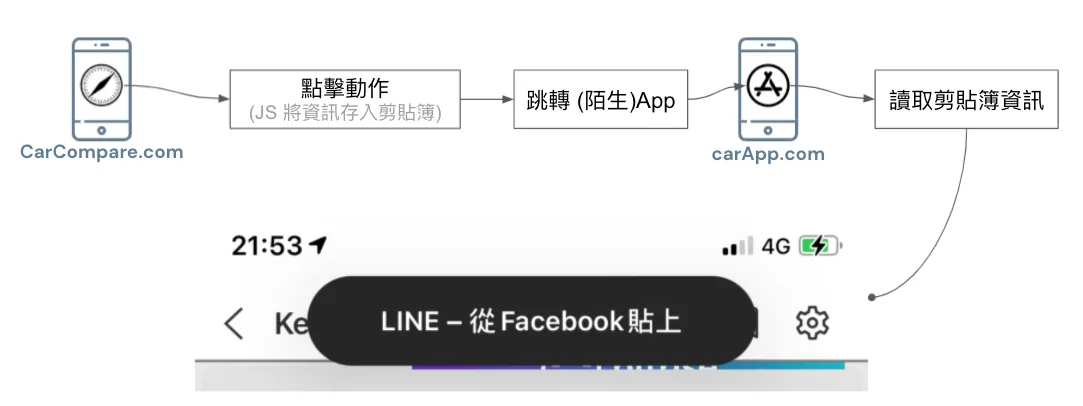
The last and only remaining method — Pasteboard:
Use the clipboard to connect cross-platform information, as Apple cannot disable clipboard use across apps, but it can notify the user.
⚠️ iOS >= 14 Added Clipboard Access Warning
⚠️ 2022/07/22 Update: iOS 16 Upcoming Changes
Starting from iOS 16, when an app reads the clipboard without the user actively pasting, a prompt will appear. The user must allow it for the app to access the clipboard content.
UIPasteBoard’s privacy change in iOS 16
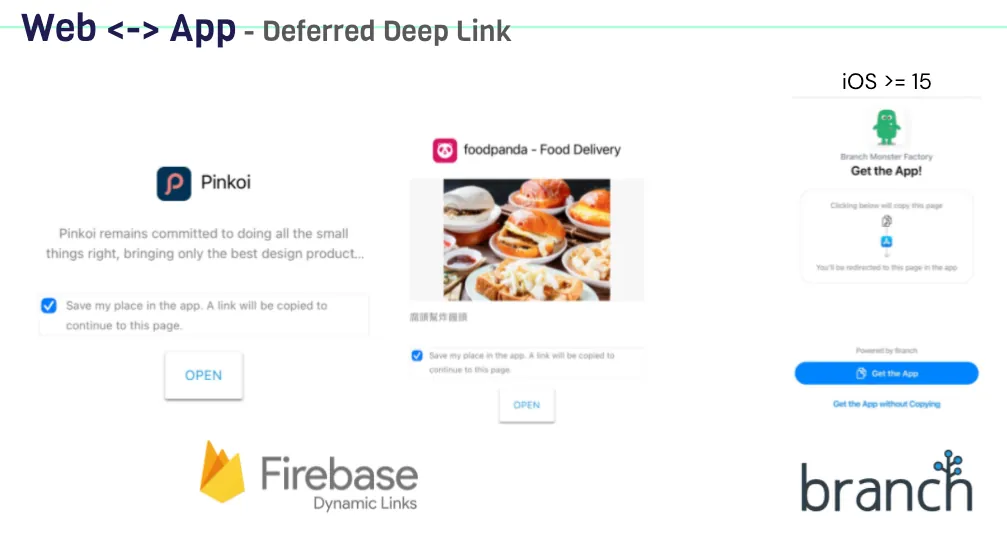
Implementing Deferred Deep Link Using Pasteboard
Here, I want to emphasize the privacy concerns regarding the iOS 14 clipboard. For more details, please refer to my previous article “iOS 14 Clipboard Privacy Panic: The Dilemma Between Privacy and Convenience“
Although reading the clipboard might raise concerns about data theft, more often it is our app’s way of providing a better user experience:
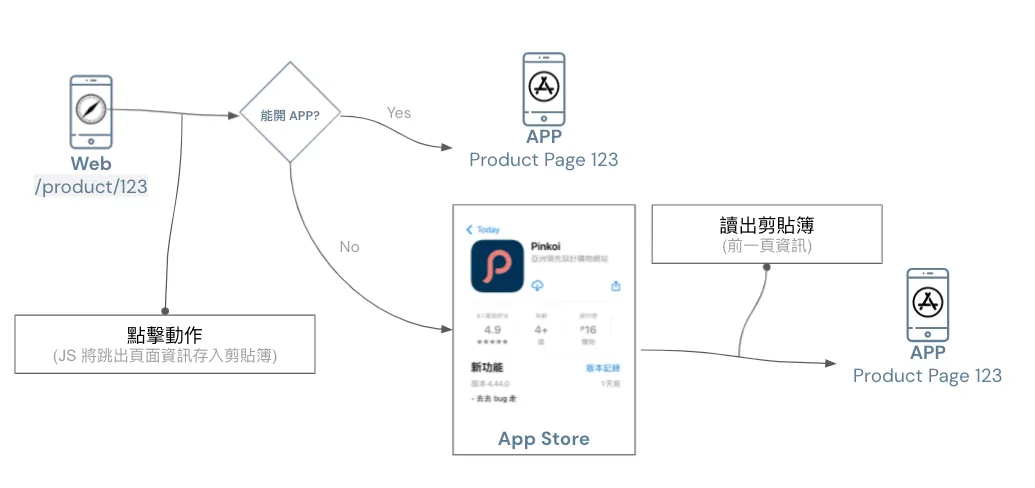
Before implementing Deferred Deep Link, when guiding users to install the app from a website, opening the app after installation will by default only open the homepage; a better user experience should open the app to the corresponding page that matches the webpage the user was on.
To achieve this function, the website and app need a way to connect data. Since other methods mentioned earlier have been blocked, the clipboard is currently the only medium for storing information (as shown above).
Including Firebase Dynamic Links and the latest version of Branch.io (previously Branch.io used IP Address Fingerprint for implementation) also use the clipboard for Deferred Deep Link.
Implementation can refer to my previous article: iOS Deferred Deep Link 延遲深度連結實作(Swift)
Generally, to achieve Deferred Deep Linking, clipboard data is read only the first time the app opens or when returning to the app; it is not accessed during use or at unusual times, which is worth noting.
A better approach is to first use UIPasteboard.general.detectPatterns to detect whether the clipboard data is what we need before reading it.
iOS ≥ 15 has optimized clipboard notifications. If the paste action is initiated by the user, the prompt will no longer appear!
Advertising Effectiveness Solutions
As mentioned earlier about Apple’s privacy principles, the goal is balance, not completely blocking users from services.
Website and Website Advertising Performance Statistics:
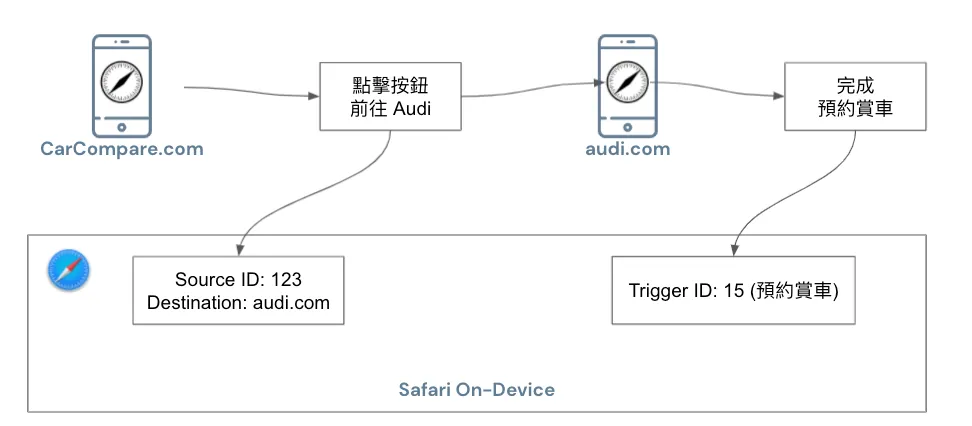
Safari’s counterpart to blocking Intelligent Tracking Prevention is Private Click Measurement (WebKit), used to measure ad performance without compromising personal privacy.
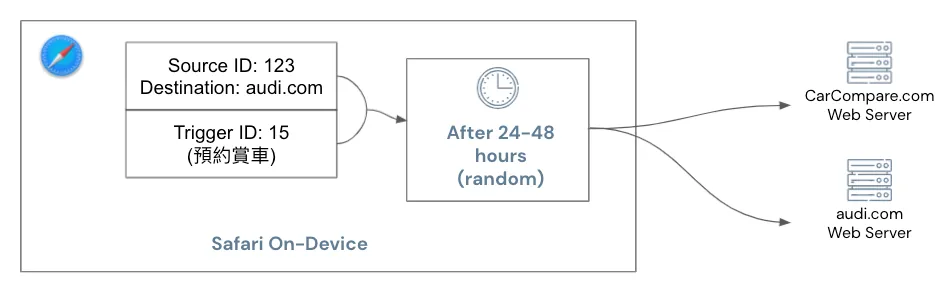
The specific process is shown in the above image. When a user clicks an ad on website A to go to website B, a Source ID (to identify the same user) and Destination information (target website) are recorded in the browser; when the user completes a conversion on website B, a Trigger ID (representing the action) is also recorded in the browser.
These two pieces of information will be combined and sent to websites A and B after a random 24 to 48 hours to obtain advertising performance.
Everything is handled on-device by Safari itself, and protection against malicious clicks is also provided by Safari.
Ad Performance Statistics Between Apps and Websites or Apps:
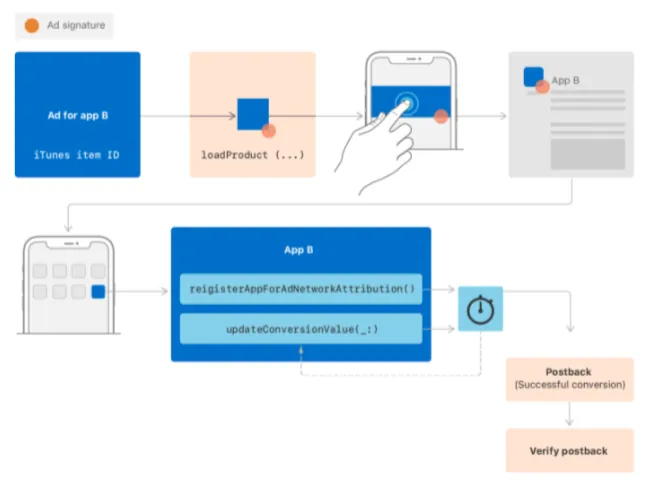
You can use SKAdNetwork (requires application to Apple) similar to Private Click Measurement, which will not be further elaborated here.
It can be emphasized that Apple is not working alone; SKAdNetwork has now reached version 2.0. Apple continues to collect developers’ and advertisers’ needs while integrating personal privacy controls, continuously enhancing the SDK’s features.
I sincerely hope Deferred Deep Link can be integrated via SDK, as our goal is to enhance user experience without infringing on personal privacy.
For technical details, refer to “WWDC 2021 — Meet privacy-preserving ad attribution”.
Cross-Platform
All iOS ≥ 13 apps that support third-party login must implement Sign in with Apple, or they cannot be successfully published on the App Store
Name can be edited freely
Can hide the real email (use Apple-generated virtual email instead)
Users can request account deletion App must implement this by 2022/01/31 🆕
iOS >= 15 iCloud+ Users Support Hide My Email
Supports all email fields in Safari and apps
Users can freely generate virtual email addresses in the settings.
Like Sign in with Apple, use Apple’s generated virtual email instead of your real email. When you receive emails, Apple forwards them to your real inbox, protecting your email information.
Similar to 10-minute mail, but more powerful; as long as you keep using it, that virtual mailbox address is yours permanently; there is no limit on adding new addresses, you can create unlimited ones. Not sure how Apple prevents abuse.
Settings -> Apple ID -> Hide My Email
Others
App privacy details on the App Store:
Apps must disclose on the App Store which user data will be tracked and how it will be used .
For detailed information, please refer to: “App privacy details on the App Store”.
Fine Control of Personal Privacy Data:
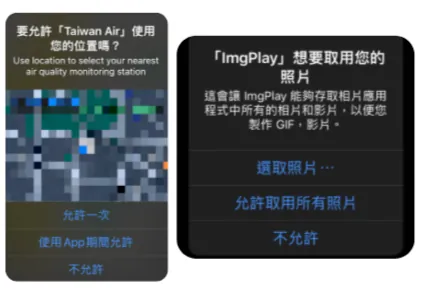
iOS ≥ 14 allows finer control over location and photo access, such as granting permission to only specific photos or allowing location access only while the app is in use.
iOS ≥ 15 introduces the CLLocationButton to enhance user experience. It lets users get their current location by tapping the button without prior permission or consent. This button is not customizable and can only be activated by user interaction.
Personal Privacy Access Notice:
iOS ≥ 15 adds personal privacy access prompts, such as for clipboard, location, camera, and microphone
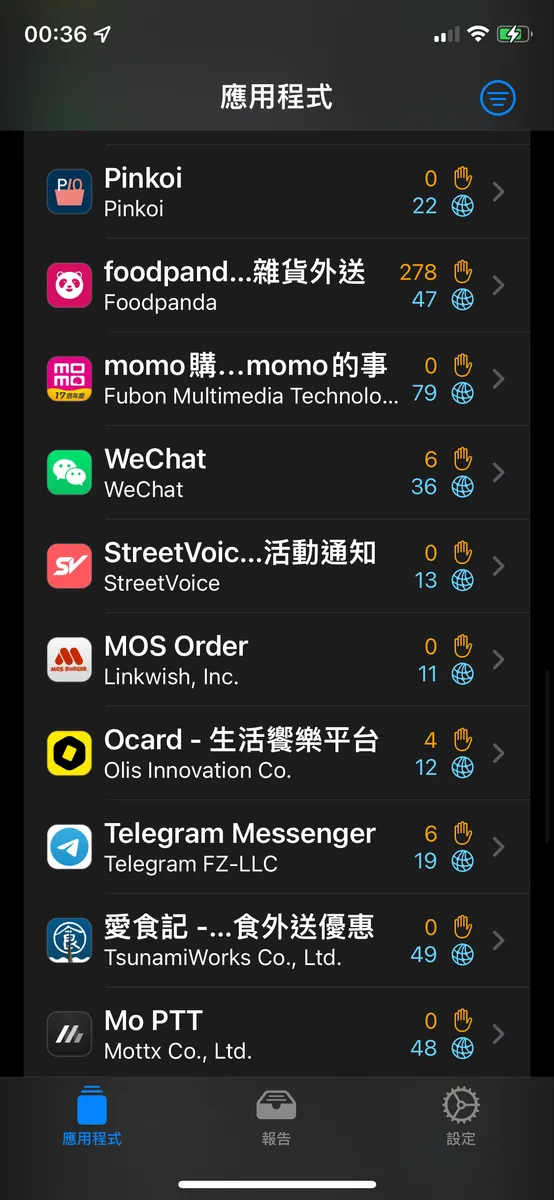
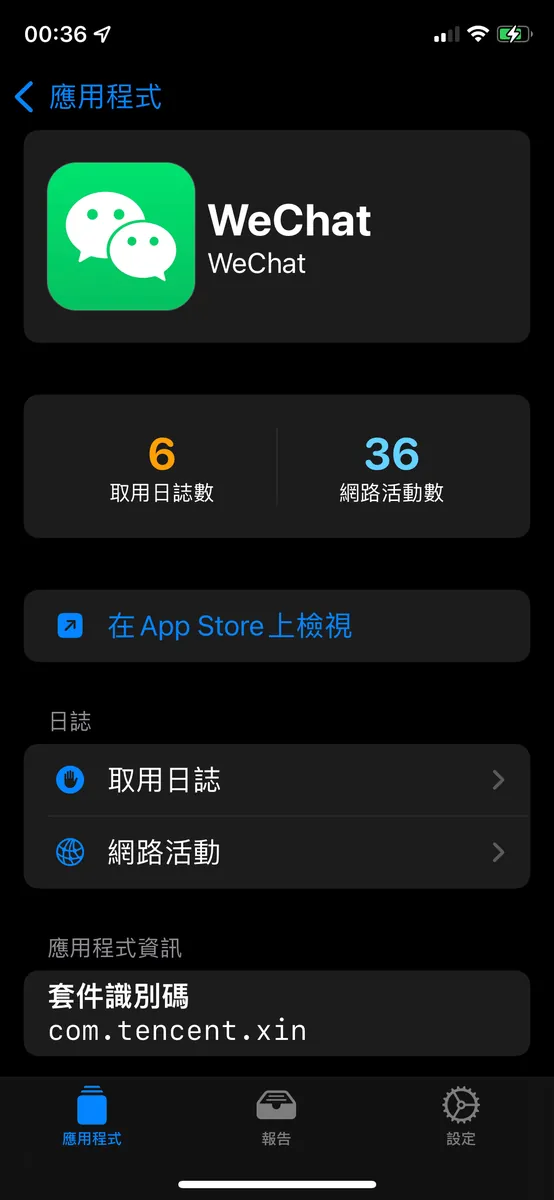
App Privacy Report:
iOS ≥ 15 allows exporting a report of all apps’ privacy-related feature usage and network activity from the past 7 days.
Since the report file is a
.ndjsonplain text file, it is not easy to view directly; you can first download the “Privacy Insights” app from the App Store to view the report.Go to Settings -> Privacy -> Scroll to the bottom “Record App Activity” -> Enable Record App Activity
Save App Activity
Select “Import to Privacy Insights”
After importing, you can view the privacy report immediately.
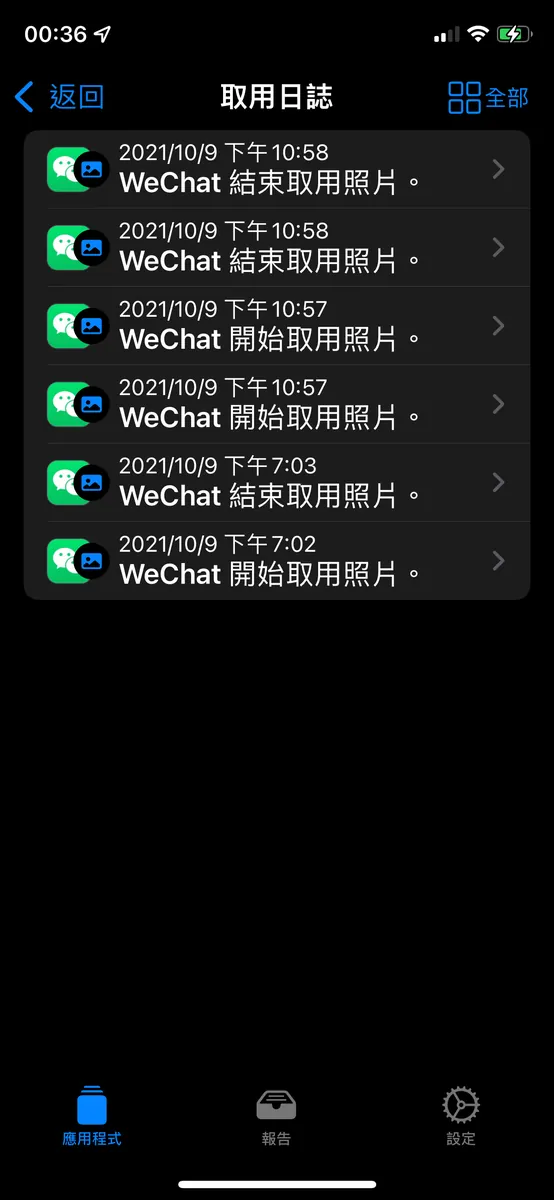
As mentioned in the news, WeChat does secretly read photo information in the background when the app is reopened.
Also, I found several Chinese apps that secretly perform tasks, so I disabled all their permissions in the settings.
If it weren’t for this feature that exposes them, we wouldn’t know how long our data has been stolen!
Recap
Apple’s privacy principles
After reviewing the changes to privacy features over the years, let’s take a look back at Apple’s privacy principles:
Data Minimization: Apple uses technology to limit access to only the necessary data.
On-Device Processing: Private data is not uploaded to the cloud; all processing happens locally. Examples include Safari Private Click Measurement, Apple’s machine learning SDK CoreML, which also runs locally, Siri/Live Text in Camera on iOS ≥ 15, Apple Maps, News, photo recognition features, and more.
User Transparency and Control: New privacy access prompts, logging reports, and detailed privacy control features.
Security: Data storage and transmission security, preventing misuse of UserDefault, iOS 15 supports end-to-end encryption and decryption with CryptoKit, transmission security with Private Relay.
Fragmented Data
Back to the very beginning, using technical methods to piece together Harry’s connection map, websites and apps are blocked from linking to each other, leaving only copy-paste usable, but with warnings.
Personal data from service registration and third-party login can be protected by using Sign in with Apple and the Hide My Email feature; alternatively, use native iOS apps more frequently.
Could Offline Events Help Modify Apple Card to Prevent Privacy Leaks?
No one has any chance to piece together Harry’s activity outline anymore.
Apple is People-Centered
Therefore, “people-oriented” is the motto I associate with Apple. Going against the commercial market requires strong conviction. Related to this, “technology-oriented” is the motto I associate with Google, as Google consistently creates many geeky tech projects. Lastly, “business-oriented” is the motto I associate with Facebook, as FB often focuses solely on commercial profit in many aspects.
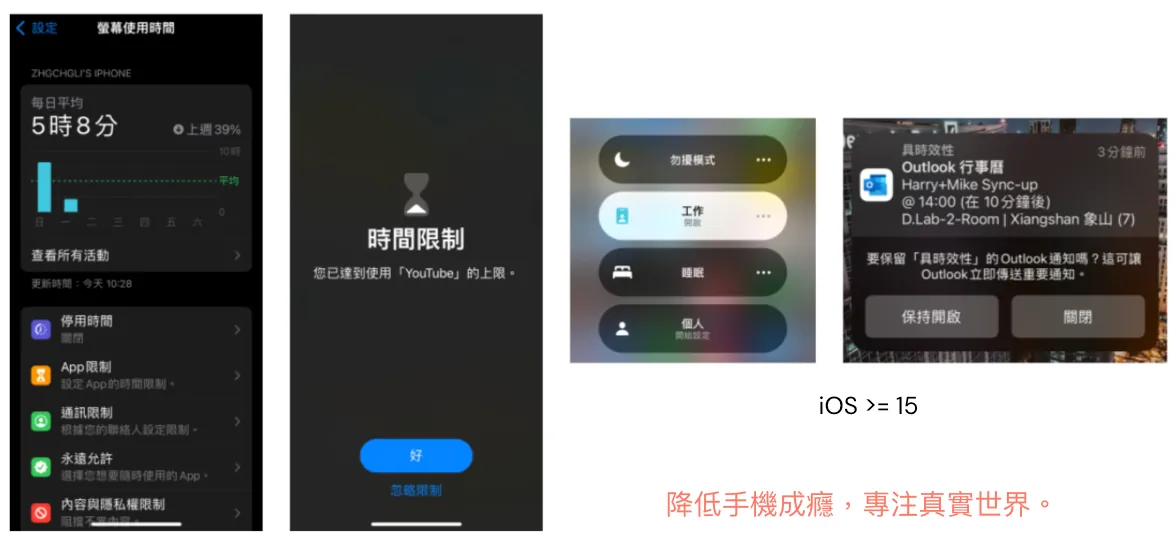
Besides adjustments to privacy features, iOS has continuously enhanced its tools to prevent phone addiction in recent years, introducing features like “Screen Time Reports,” “App Usage Limits,” and “Focus Mode” to help users break free from phone addiction.
Finally, I hope everyone can
Value Personal Privacy
Not Controlled by Capital
Reduce Virtual Addiction
Preventing Social Decline
Live a Brilliant Life in the Real World!
Private Relay/IDFA/Pasteboard/Location Testing Project:
References
If you have any questions or suggestions, feel free to contact me.
This post was originally published on Medium (View original post), and automatically converted and synced by ZMediumToMarkdown.


{:target="_blank"} | [Pinkoi, We Are Hiring!](https://www.pinkoi.com/about/careers){:target="_blank"}](/assets/9a05f632eba0/1*gYucHdBa4tyd9lX5eyr08w.webp)
{:target="_blank"}](/assets/9a05f632eba0/1*ZDX3oYcoHwSh0Lkb1g1X_g.webp)
{:target="_blank"}](/assets/9a05f632eba0/1*Dz-GYDKsdXQal_PausrHMA.webp)
{:target="_blank"}](/assets/9a05f632eba0/1*2LpAXuZduLStmS2tRVdcXQ.webp)
{:target="_blank"}](/assets/9a05f632eba0/1*7Kyfq0LT1mkPAFxwkmpMRQ.webp)


{:target="_blank"}](/assets/9a05f632eba0/1*Y95go0uE0DC5lqAAJ9N96Q.webp)